<< Назад на страницу выбора модели

| Firewall throughput (1518bytes) | 1.92 Tbit/s |
| Firewall throughput (IMIX) | 1.92 Tbit/s | |
| Maximum number of concurrent sessions | 2,560,000,000 | |
| IPSec VPN performance (AES) | 1400 Gbit/s | |
| Maximum number of concurrent IPSec VPN tunnels | 1,000,000 | |
| Number of expansion slots | 16 | |
| Number of MPU slots | 2 | |
| Interface types | GE, 10GE, 40GE, and 100GE interfaces | |
| SPU | Firewall and application security SPUs | |
| Dimensions (H × W × D, mm) | 1420 × 442 × 650 (32U) | |
| Weight (Full configuration) | Empty: 94.4 kg Full configuration: 233.9 kg | |
| AC power supply | 90 V AC to 264 V AC; 175 V AC to 264 V AC (recommended) | |
| DC power supply | -72 V to -38 V; -48 V (rated) | |
| Power | Typical: 7387W(DC) Typical: 7858W(AC) Most: 8930W(DC) Most: 9500W(AC) | |
| Working temperature | Extended operation: 0°C to 45°C Storage: -40°C to +70°C | |
| Ambient humidity | Long term: 5% RH to 85% RH, non-condensing Short term: 5% RH to 95% RH, non-condensing |

| Function | Description |
| Comprehensive protection | Provides integrated control and protection based on application, content, time, user, attack, and location (ACTUAL). The application-layer protection and application identification are combined. For example, the USG9500 can identify Oracle-specific traffic and implement intrusion prevention accordingly to increase efficiency and reduce false positives |
| Based on application | Accurately identifies over 6000 applications (including mobile and web applications) and their services, and then implements access control and service acceleration accordingly. For example, the USG9500 can identify the voice and data services of an instant messaging application and apply different control policies to the services |
| Based on user | Supports eight user authentication methods, including RADIUS, LDAP, and AD authentication, synchronization of user information from an existing user authentication system, userbased access control, and QoS management |
| Based on location | Uses IP address geolocation to identify from where application and attack traffic originates, promptly detects network anomalies, and implements differentiated user-defined access control for traffic from different locations |
| Versatility | Integrates traditional firewall functions, VPN, intrusion prevention, antivirus, data leak prevention (DLP), bandwidth management, and online behavior management into one device to simplify deployment and improve efficiency |
| Intrusion prevention system (IPS) | Data leak prevention based on content awareness File reassembly and data filtering for more than 30 file types (including Word, Excel, PPT, and PDF), and file blocking for more than 120 file types |
| Antivirus (AV) | Prevents over 5 million viruses and Trojan horses using the high-performance antivirus engine and the daily-updated virus signature database |
| Data leak prevention | Identifies and filters file and content transfers. The USG9500 can identify more than 120 file types, regardless of whether file name extensions are maliciously changed. In addition, the USG9500 can restore and implement content filtering for over 30 types of files, such as Word, Excel, PPT, PDF, and RAR files, to prevent leaks of critical enterprise information |
| SSL decryption | Serves as a proxy to perform application-layer protection, such as IPS, AV, DLP, and URL filtering, for SSL-encrypted traffic |
| Anti-DDoS | Identifies and prevents 10 types of DDoS attacks, such as SYN and UDP flood attacks |
| Online behavior management | Implements cloud-based URL filtering to prevent threats from malicious websites by using a URL category database that contains 85 million URLs, controls online behaviors such as posting to social media and FTP upload and download, and audits Internet access records |
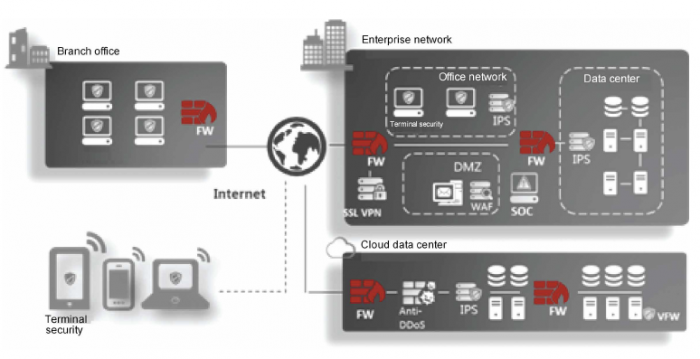
| Secure interconnection | Supports various VPN features, such as IPSec, L2TP, MPLS, and GRE VPN, to ensure secure and reliable connections between enterprise headquarters and branch offices |
| QoS management | Flexibly manages the upper and lower traffic thresholds and supports applicationspecific policy-based routing and QoS marking to preferentially forward traffic of specified URL categories, such as financial websites |
| Load balancing | Supports server load balancing, such as load balancing based on link quality, bandwidth, and weight in scenarios where multi-egresses are available |
Security Features
Basic Firewall Functions
Transparent, routing, and hybrid modes
Stateful inspection
Blacklist and whitelist
Access control
Application specific packet filter (ASPF)
Security zones
Egress Load Balancing
ISP-based routing
Intelligent uplink selection
Transparent DNS proxy at egress
User-based traffic control
Application-based traffic control
Link-based traffic control
Time-based traffic control
Ingress Load Balancing
Intelligent DNS at ingress
Server load balancing
Application-based QoS
URL Filtering
URL database of 85 million URLs
80+ URL categories
Trend and top N statistics based on users, IP addresses, categories, and counts
Query of URL filtering logs
VPN
DES, 3DES, and AES encryption
MD5 and SHA-1 authentication
Manual key, PKI (X509), and IKEv2
Perfect forward secrecy (DH group)
Anti-replay
Transport and tunnel modes
IPSec NAT traversal
Dead peer detection (DPD)
EAP authentication
EAP-SIM, EAP-AKA
VPN gateway redundancy
IPSec v6, IPSec 4 over 6, and IPSec 6 over 4
L2TP tunnel
GRE tunnel
Anti-DDoS
Prevention of SYN, ICMP, TCP, UDP, and DNS floods
Prevention of port scan, Smurf, teardrop, and IP sweep attacks
Prevention of attacks exploiting IPv6 extension headers
TTL detection
TCP-mss detection
Attack logs
High Availability
Multi-DC cluster
Active/active and active/standby modes
Hot standby (Huawei redundancy protocol)
Configuration synchronization
Data backup between SPUs in a chassis
Firewall and IPSec VPN session synchronization
Device fault detection
Link fault detection
Dual-MPU switchover
Management
Web UI (HTTP/HTTPS)
CLI (console)
CLI (remote login)
CLI (SSH)
U2000/VSM network management system
Hierarchical administrators
Software upgrade
Configuration rollback
STelnet and SFTP
Certification
Safety certification
Electro Magnetic Compatibility (EMC) certification
CB, Rohs, FCC, MET, C-tick, and VCCI certification
ICSA Labs: Firewalls, IPS, IPSec, SLL-TLS, Anti-Virus
NAT/CGN
Destination NAT/PAT
NAT NO-PAT
Source NAT-IP address persistency
Source IP address pool groups
NAT server
Bidirectional NAT
NAT-ALG
Unlimited IP address expansion
Policy-based destination NAT
Port range allocation
Hairpin connections
SMART NAT
NAT64
DS-Lite
IPv6 rapid deployment (6RD)
Service Awareness
Identification and prevention of over 6000 protocols:
P2P, IM, game, stock charting/trading, VoIP, video, stream media, email, mobile phone services, Web browsing, remote access, network management, and news applications
Antivirus
Detection of 5 million viruses
Flow-based inspection for higher performance
Inspection of encrypted traffic
Trend and top N statistics by virus family
PKI
Online CA certificate enrollment
Online CRL check
Hierarchical CA certificates
Support for public-key cryptography standards (PKCS#10 protocol)
CA certificate
Support for SCEP, OCSP, and CMPv2 protocols
Self-signed certificates
Intrusion Prevention System
Protocol anomaly detection
User-defined signatures
Automatic update of the knowledge bases
Zero-day attack defense
Prevention of worms, Trojan horses, and malware attacks
Networking/Routing
Support for POS, GE, and 10GE interfaces
DHCP relay/server
Policy-based routing
IPv4/IPv6 dynamic routing protocols, such as RIP, OSPF, BGP, and IS-IS
Interzone/inter-VLAN routing
Link aggregation, such as Eth-trunk and L ACP
Virtual System
Up to 4095 virtual systems (VSYS)
VLAN on virtual systems
Security zones on virtual systems
User-configurable resources on virtual systems
Inter-virtual system routing
Virtual system-specific Committed Access Rate (CAR)
Separate management of virtual systems
Resource isolation for different tenants
Logging/Monitoring
Structured system logs
SNMPv2
Binary logs
Traceroute
Log server (LogCenter)
User Authentication and Access Control
Built-in (internal) database
RADIUS accounting
Web-based authentication